Which of the following can Peter, a security administrator, use to distribute the processing effort when generating hashes for a password cracking program?
A. RAID
B. Clustering
C. Redundancy
D. Virtualization
CompTIA exam questions
Which of the following can Peter, a security administrator, use to distribute the processing effort when generating hashes for a password cracking program?
A. RAID
B. Clustering
C. Redundancy
D. Virtualization
Digital certificates can be used to ensure which of the following? (Select TWO).
A. Availability
B. Confidentiality
C. Verification
D. Authorization
E. Non-repudiation
A security administrator has just finished creating a hot site for the company. This implementation relates to which of the following concepts?
A. Confidentiality
B. Availability
C. Succession planning
D. Integrity
Which of the following concepts allows an organization to group large numbers of servers together in order to deliver a common service?
A. Clustering
B. RAID
C. Backup Redundancy
D. Cold site
The use of social networking sites introduces the risk of:
A. Disclosure of proprietary information
B. Data classification issues
C. Data availability issues
D. Broken chain of custody
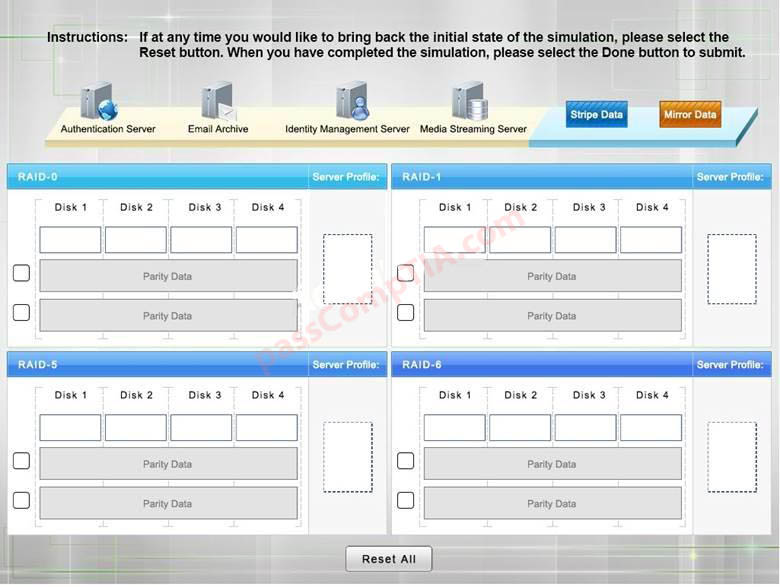
A security administrator is given the security and availability profiles for servers that are being deployed.
1) Match each RAID type with the correct configuration and MINIMUM number of drives.
2) Review the server profiles and match them with the appropriate RAID type based on integrity, availability, I/O, storage requirements.
Instructions:
• All drive definitions can be dragged as many times as necessary
• Not all placeholders may be filled in the RAID configuration boxes
• If parity is required, please select the appropriate number of parity check boxes
• Server profiles may be dragged only once
If at any time you would like to bring back the initial state of the simulation, please select the Reset
button. When you have completed the simulation, please select the Done
The Chief Information Officer (CIO) has noticed the corporate wireless signal is available in the parking lot. Management requests that the wireless network be changed so it is no longer accessible in public areas, without affecting the availability inside the building. Which of the following should be changed on the network?
A. Power levels
B. Overcapacity
C. Distance limitations
D. Channel overlap
Upon arrival at work, an administrator is informed that network users cannot access the file server. The administrator logs onto the server and sees the updates were automatically installed and the network connection shows limited and no availability. Which of the following needs to be rolled back?
A. The browser on the server
B. The server’s NIC drivers
C. The server’s IP address
D. The antivirus updates
A customer has engaged a company to improve the availability of all of the customer’s services and applications, enabling the customer to minimize downtime to a few hours per quarter. Which of the following will document the scope of the activities the company will provide to the customer, including the intended outcomes?
A. MLA
B. MOU
C. SOW
D. SLA
Network segmentation provides which of the following benefits?
A. Security through isolation
B. Link aggregation
C. Packet flooding through all ports
D. High availability through redundancy