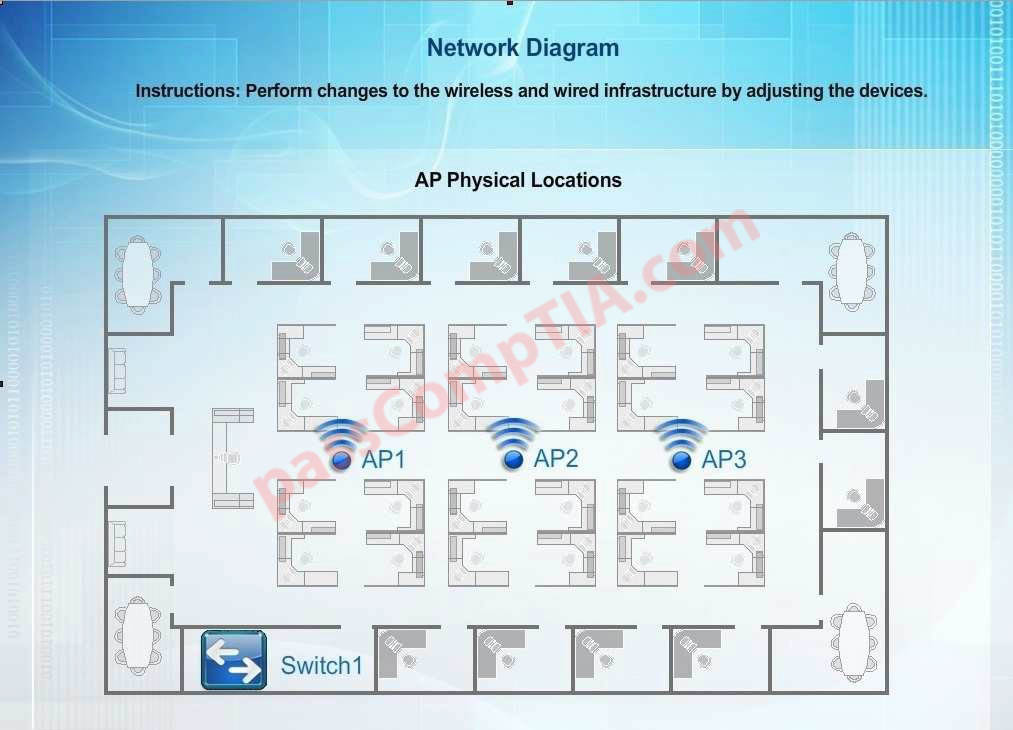
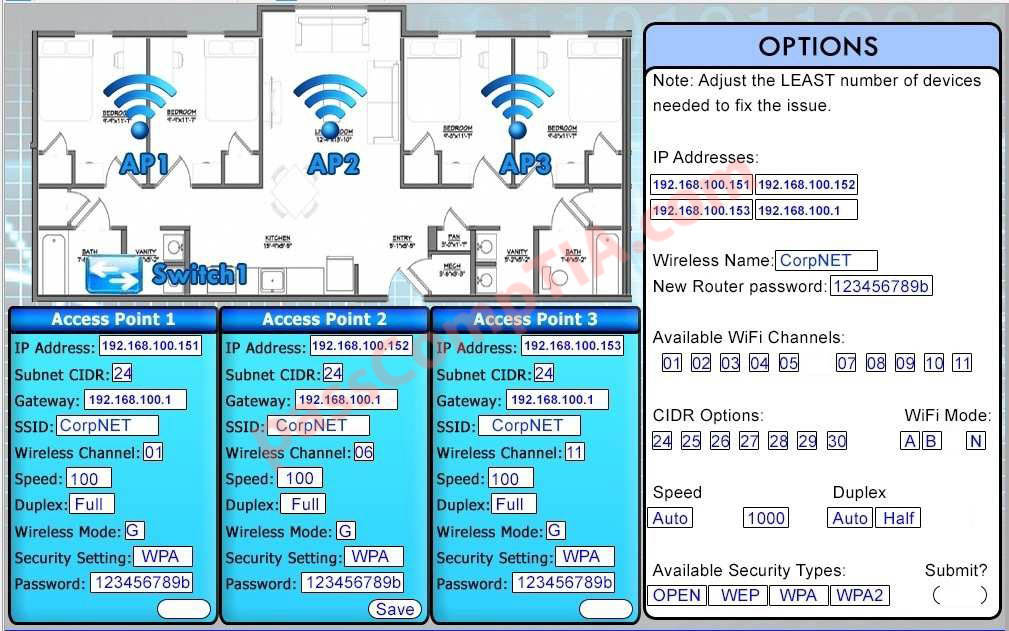
A wireless network technician for a local retail store is installing encrypted access points within the store for real-time inventory verification, as well as remote price checking capabilities, while employees are away from the registers. The store is in a fully occupied strip mall that has multiple neighbors allowing guest access to the wireless networks. There are a finite known number of approved handheld devices needing to access the store’s wireless network. Which of the following is the BEST security method to implement on the access points?
A. Port forwarding
B. MAC filtering
C. TLS/TTLS
D. IP ACL