An administrator is concerned that a company’s web server has not been patched. Which of the following would be the BEST assessment for the administrator to perform?
A. Vulnerability scan
B. Risk assessment
C. Virus scan
D. Network sniffer
CompTIA exam questions
An administrator is concerned that a company’s web server has not been patched. Which of the following would be the BEST assessment for the administrator to perform?
A. Vulnerability scan
B. Risk assessment
C. Virus scan
D. Network sniffer
When an order was submitted via the corporate website, an administrator noted special characters (e.g., “;–” and “or 1=1 –“) were input instead of the expected letters and numbers.
Which of the following is the MOST likely reason for the unusual results?
A. The user is attempting to highjack the web server session using an open-source browser.
B. The user has been compromised by a cross-site scripting attack (XSS) and is part of a botnet performing DDoS attacks.
C. The user is attempting to fuzz the web server by entering foreign language characters which are incompatible with the website.
D. The user is sending malicious SQL injection strings in order to extract sensitive company or customer data via the website.
During a security assessment, an administrator wishes to see which services are running on a remote server. Which of the following should the administrator use?
A. Port scanner
B. Network sniffer
C. Protocol analyzer
D. Process list
The system administrator is reviewing the following logs from the company web server:
12:34:56 GET /directory_listing.php?user=admin&pass=admin1
12:34:57 GET /directory_listing.php?user=admin&pass=admin2
12:34:58 GET /directory_listing.php?user=admin&pass=1admin
12:34:59 GET /directory_listing.php?user=admin&pass=2admin
Which of the following is this an example of?
A. Online rainbow table attack
B. Offline brute force attack
C. Offline dictionary attack
D. Online hybrid attack
A security administrator discovers that an attack has been completed against a node on the corporate network. All available logs were collected and stored.
You must review all network logs to discover the scope of the attack, check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. The environment is a critical production environment; perform the LEAST disruptive actions on the network, while still performing the appropriate incident responses.
Instructions: The web server, database server, IDS, and User PC are clickable. Check the box of the node(s) that have been compromised and drag and drop the appropriate actions to complete the incident response on the network. Not all actions may be used, and order is not important. If at anytime you would like to bring back the initial state of the simulation, please select the Reset button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

HOTSPOT
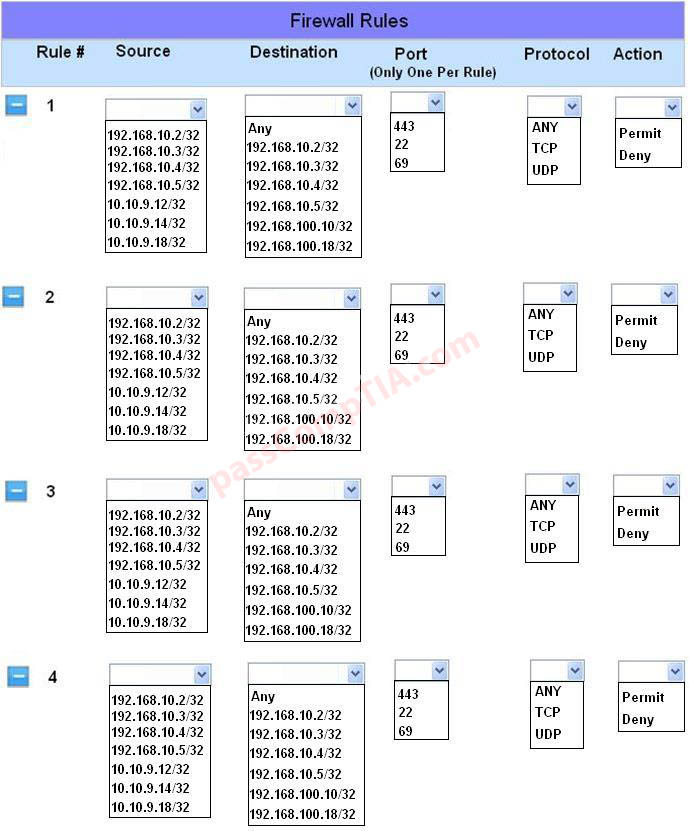
The security administrator has installed a new firewall which implements an implicit DENY policy by default Click on the firewall and configure it to allow ONLY the following communication.
1. The Accounting workstation can ONLY access the web server on the public network over the default HTTPS port. The accounting workstation should not access other networks.
2. The HR workstation should be restricted to communicate with the Financial server ONLY, over the default SCP port
3. The Admin workstation should ONLY be able to access the servers on the secure network over the default TFTP port.
Instructions: The firewall will process the rules in a top-down manner in order as a first match. The port number must be typed in and only one port number can be entered per rule Type ANY for all ports. The original firewall configuration can be reset at any time by pressing the reset button. Once you have met the simulation requirements, click save and then Done to submit.


A network technician needs to set up two public facing web servers and watns to ensure that if they are compromised the intruder cannot access the intranet. Which of the following security techniques should be used?
A. Place them behind honeypots
B. Place them in a separate subnet
C. Place them between two internal firewalls
D. Place them in the demilitarized zone
A network technician needs to separate a web server listening on port 80 from the internal LAN and secure the server from the public Internet. The web server should be accessible to the public Internet over port 80 but not the private LAN. Currently, the network is segmented with a network-based firewall using the following IP addressing scheme on each interface:
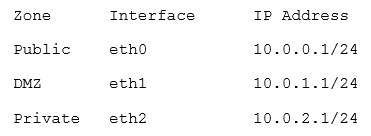
Which of the following ones should the technician use to place the web server and which of the following firewall rules should the technician configure?
A. Place the web server in the public zone with an inbound rule from eth0 interface to accept traffic over port 80 designated to the web server
B. Place the web server in the DMZ with an inbound rule from eth0 interface to eth1 to accept traffic over port 80 designated to the web server
C. Place the web server in the private zone with an inbound rule from eth2 interface to eth1 to accept traffic over port 80 designated to the web server
D. Place the web server in the DMZ with an inbound rule from eth1 interface to eth0 to accept traffic over port 80 designated to the web server
Users are reporting their network is extremely slow. The technician discovers pings to external host have excessive response times. However, internal pings to printers and other PCs have acceptable response times. Which of the following steps should the technician take NEXT?
A. Determine if any network equipment was replaced recently
B. Verify malware has not disabled the users’ PC firewalls
C. Replace users’ network cables with known-good network cables
D. Power cycle the web server
An outside organization has completed a penetration test for a company. One of the items on the report is reflecting the ability to read SSL traffic from the web server. Which of the following is the MOST likely mitigation for this reported item?
A. Ensure patches are deployed
B. Install an IDS on the network
C. Configure the firewall to block traffic on port 443
D. Implement a VPN for employees