A security administrator is segregating all web-facing server traffic from the internal network and restricting it to a single interface on a firewall. Which of the following BEST describes this new network?
A. VLAN
B. Subnet
C. VPN
D. DMZ
CompTIA exam questions
A security administrator is segregating all web-facing server traffic from the internal network and restricting it to a single interface on a firewall. Which of the following BEST describes this new network?
A. VLAN
B. Subnet
C. VPN
D. DMZ
Peter, a network administrator, is implementing IPv6 in the DMZ. Which of the following protocols must he allow through the firewall to ensure the web servers can be reached via IPv6 from an IPv6 enabled Internet host?
A. TCP port 443 and IP protocol 46
B. TCP port 80 and TCP port 443
C. TCP port 80 and ICMP
D. TCP port 443 and SNMP
A technician is installing a surveillance system for a home network. The technician is unsure which ports need to be opened to allow remote access to the system. Which of the following should the technician perform?
A. Disable the network based firewall
B. Implicit deny all traffic on network
C. Configure a VLAN on Layer 2 switch
D. Add the system to the DMZ
A firewall ACL is configured as follows:
10. Deny Any Trust to Any DMZ eq to TCP port 22
11. Allow 10.200.0.0/16 to Any DMZ eq to Any
12. Allow 10.0.0.0/8 to Any DMZ eq to TCP ports 80, 443
13. Deny Any Trust to Any DMZ eq to Any
A technician notices that users in the 10.200.0.0/16 network are unable to SSH into servers in the DMZ.
The company wants 10.200.0.0/16 to be able to use any protocol, but restrict the rest of the 10.0.0.0/8 subnet to web browsing only. Reordering the ACL in which of the following manners would meet the company’s objectives?
A. 11, 10, 12, 13
B. 12, 10, 11, 13
C. 13, 10, 12, 11
D. 13, 12, 11, 10
A network technician needs to separate a web server listening on port 80 from the internal LAN and secure the server from the public Internet. The web server should be accessible to the public Internet over port 80 but not the private LAN. Currently, the network is segmented with a network-based firewall using the following IP addressing scheme on each interface:
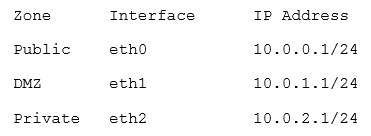
Which of the following ones should the technician use to place the web server and which of the following firewall rules should the technician configure?
A. Place the web server in the public zone with an inbound rule from eth0 interface to accept traffic over port 80 designated to the web server
B. Place the web server in the DMZ with an inbound rule from eth0 interface to eth1 to accept traffic over port 80 designated to the web server
C. Place the web server in the private zone with an inbound rule from eth2 interface to eth1 to accept traffic over port 80 designated to the web server
D. Place the web server in the DMZ with an inbound rule from eth1 interface to eth0 to accept traffic over port 80 designated to the web server
A technician just completed a new external website and setup access rules in the firewall. After some testing, only users outside the internal network can reach the site. The website responds to a ping from the internal network and resolves the proper public address. Which of the following could the technician do to fix this issue while causing internal users to route to the website using an internal address?
A. Configure NAT on the firewall
B. Implement a split horizon DNS
C. Place the server in the DMZ
D. Adjust the proper internal ACL
A technician is tasked with setting up a web server for a small business. Where would the technician place the server so that it is accessible from the Internet while keeping the customer’s network separated from it?
A. In the DMZ
B. Behind NAT
C. Outside the DHCP scope
D. Inside the DHCP scope