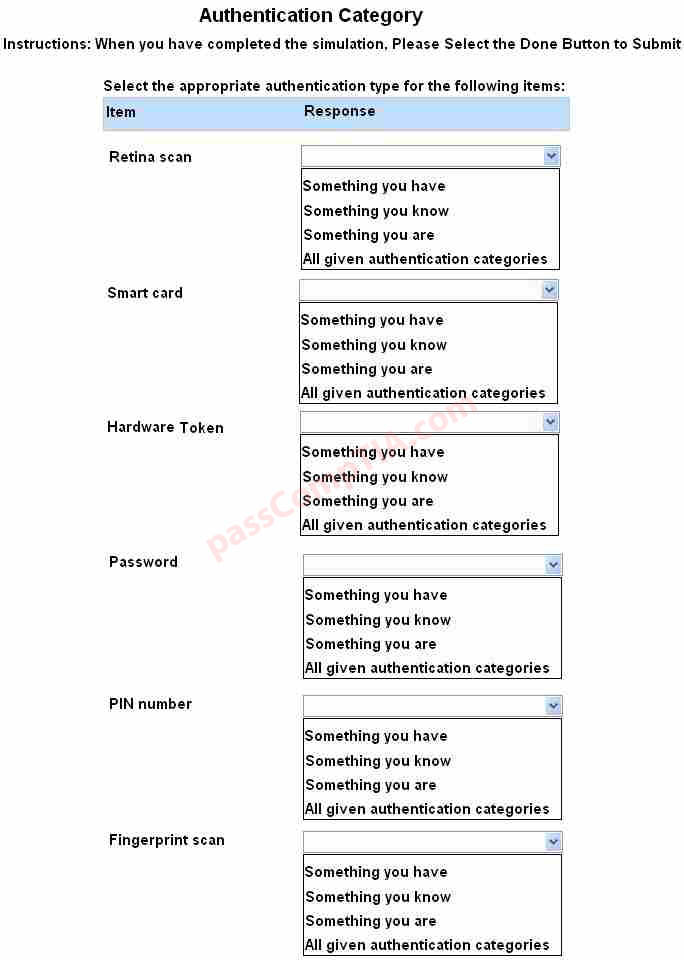
For each of the given items, select the appropriate authentication category from the drop down
choices.
Select the appropriate authentication type for the following items:
CompTIA exam questions
DRAG DROP
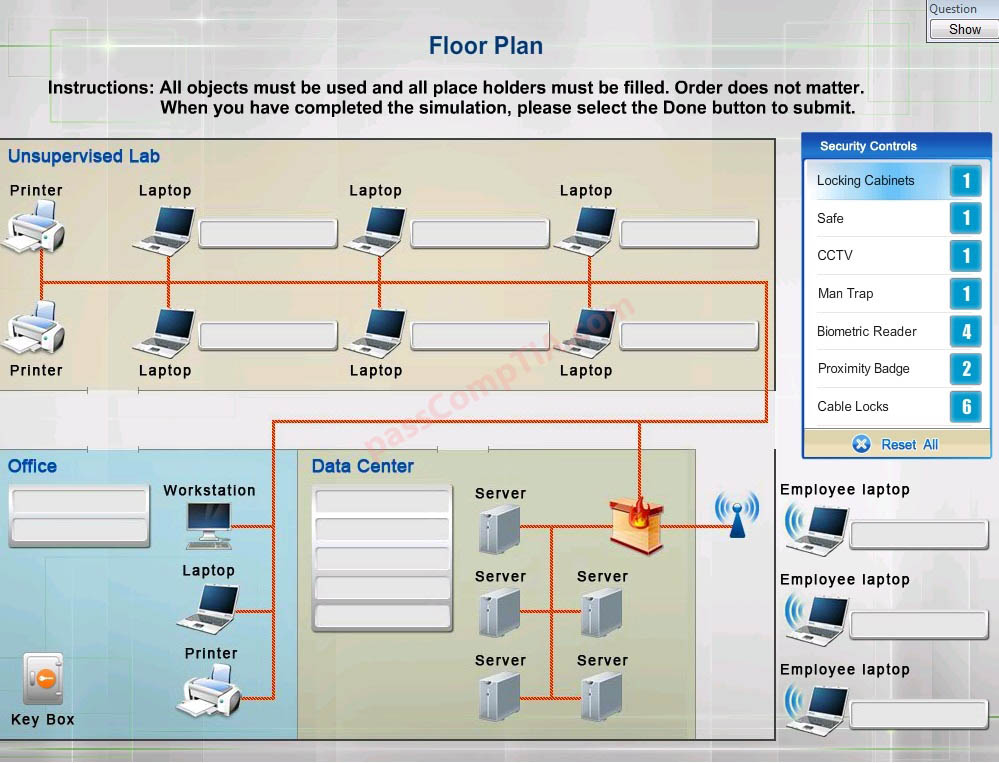
You have been tasked with designing a security plan for your company. Drag and drop the appropriate security controls on the floor plan.
Instructions:All objects must be used and all place holders must be filled. Order does not matter. When you have completed the simulation, please select the Done button to submit.
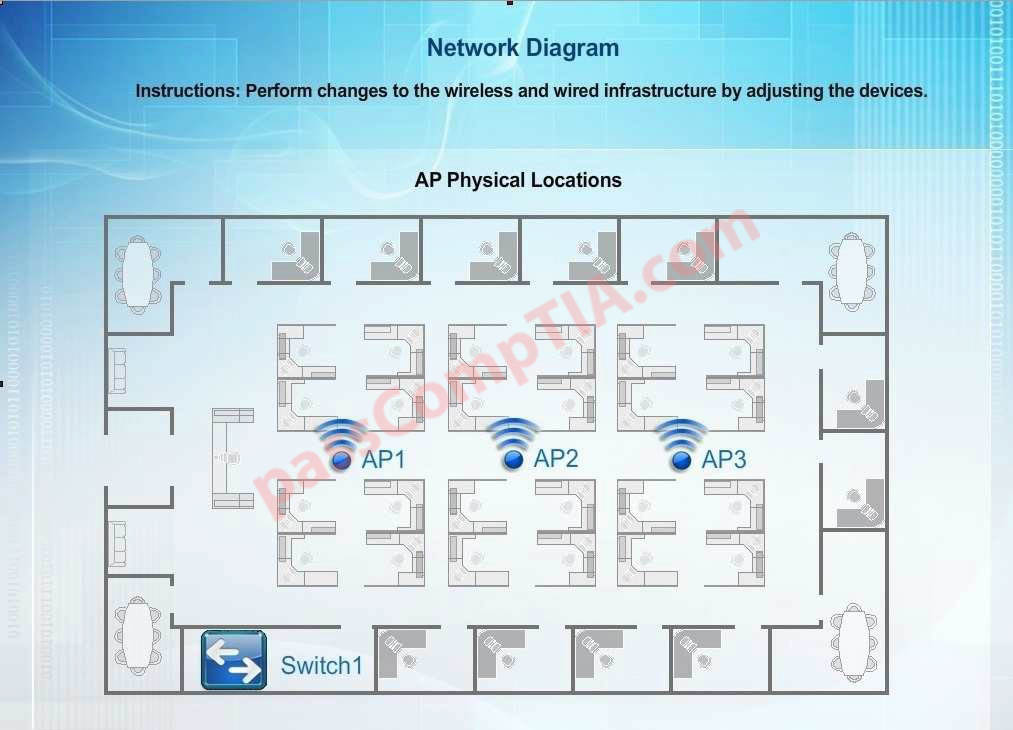
You have been tasked with setting up a wireless network in an office. The network will consist of 3 access points and a single switch. The network must meet the following parameters.
The SSIDs need to be configured as corpnet with a key of S3cr3t! The wireless signals should not interfere with each other.
The subnet the Access points and Switch are on should only support 30 devices maximum The access Points should be configured to only support TKIP clients at a maximum speed
Instructions: Click on the devices to review their information and adjust the setting of the APs to meet the given requirements.
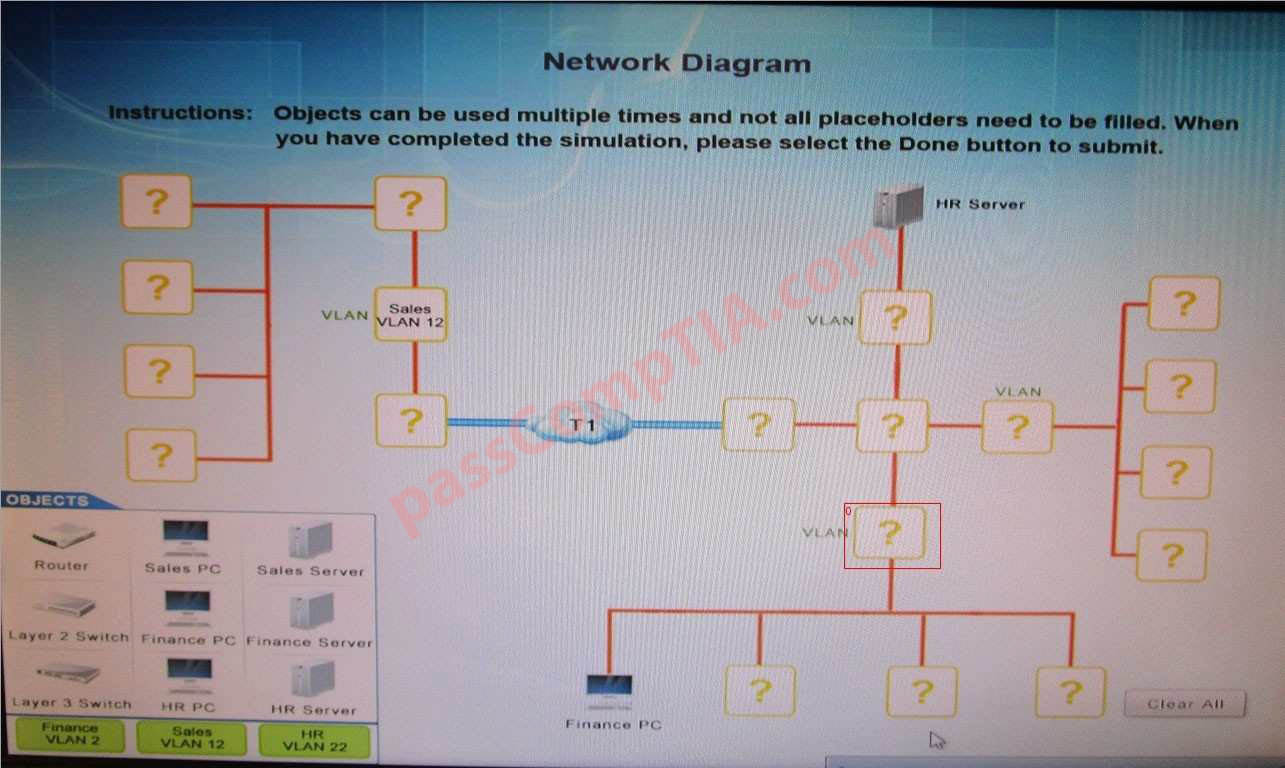
You are tasked with creating a network that will accomplish the following requirements Requirements:
1) The remote sales team must be able to connect to the corporate network
2) Each department must have ONLY two PCs and a server
3) Each department must be segmented from each other
4) The following VLANs have been designated:
a) VLAN 2- Finance
b) VLAN 12- Sales
c) VLAN 22- Human Resources (HR)
Complete the network by dragging the required objects into the diagram.
INSTRUCTIONS: Objects can be used multiple times and not all placeholders need to be filled
Select and Place: