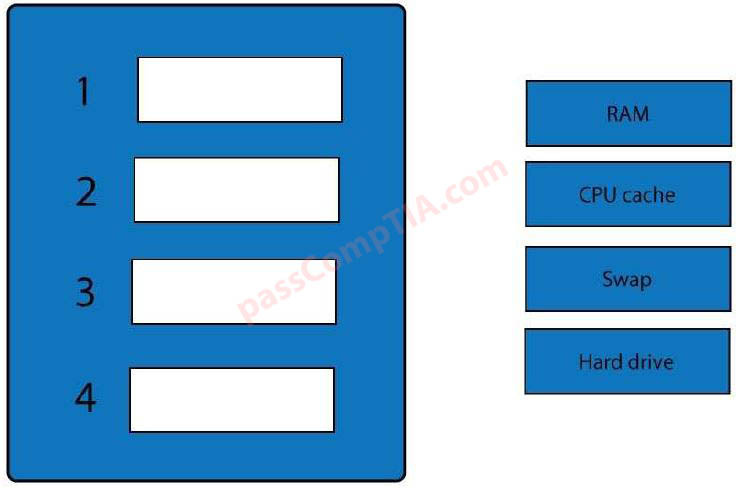
An employee has been charged with fraud and is suspected of using corporate assets. As authorities collect evidence, and to preserve the admissibility of the
evidence, which of the following forensic techniques should be used?
A. Order of volatility
B. Data recovery
C. Chain of custody
D. Non-repudiation
CompTIA Security+ Question G-69
The security manager received a report that an employee was involved in illegal activity and has saved data to a workstation’s hard drive. During the investigation, local law enforcement’s criminal division confiscates the hard drive as evidence. Which of the following forensic procedures is involved?
A. Chain of custody
B. System image
C. Take hashes
D. Order of volatility
CompTIA Security+ Question G-67
Computer evidence at a crime is preserved by making an exact copy of the hard disk. Which of the following does this illustrate?
A. Taking screenshots
B. System image capture
C. Chain of custody
D. Order of volatility
CompTIA Security+ Question B-100
Computer evidence at a crime scene is documented with a tag stating who had possession of the evidence at a given time.
Which of the following does this illustrate?
A. System image capture
B. Record time offset
C. Order of volatility
D. Chain of custody
CompTIA Security+ Question B-61
Which of the following should Jane, a security administrator, perform before a hard drive is analyzed with forensics tools?
A. Identify user habits
B. Disconnect system from network
C. Capture system image
D. Interview witnesses
CompTIA Security+ Question A-8
An incident response team member needs to perform a forensics examination but does not have the required hardware. Which of the following will allow the team member to perform the examination with minimal impact to the potential evidence?
A. Using a software file recovery disc
B. Mounting the drive in read-only mode
C. Imaging based on order of volatility
D. Hashing the image after capture