A security analyst sees some suspicious entries in a log file from a web server website, which has a form that allows customers to leave feedback on the company’s products. The analyst believes a malicious actor is scanning the web form. To know which security controls to put in place, the analyst first needs to determine the type of activity occurring to design a control. Given the log below:
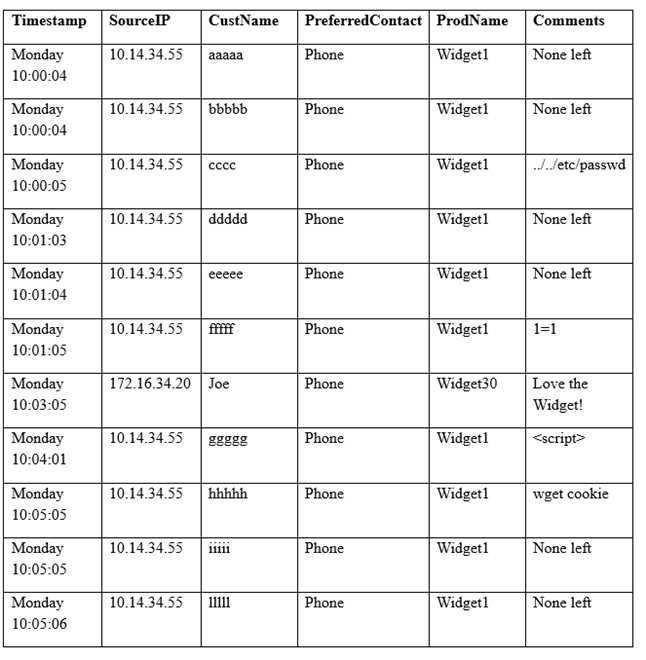
Which of the following is the MOST likely type of activity occurring?
A. SQL injection
B. XSS scanning
C. Fuzzing
D. Brute forcing
CompTIA Security+ Question L-84
A server administrator notes that a fully patched application often stops running due to a memory error. When reviewing the debugging logs they notice code being run calling an internal process to exploit the machine. Which of the following attacks does this describes?
A. Malicious add-on
B. SQL injection
C. Cross site scripting
D. Zero-day
CompTIA Security+ Question K-100
Which of the following types of application attacks would be used to specifically gain unauthorized information from databases that did not have any input validation implemented?
A. SQL injection
B. Session hijacking and XML injection
C. Cookies and attachments
D. Buffer overflow and XSS
CompTIA Security+ Question K-21
Peter, the security administrator, has been notified by the IDS that the company website is under attack. Analysis of the web logs show the following string, indicating a user is trying to post a comment on the public bulletin board.
INSERT INTO message `
This is an example of which of the following?
A. XSS attack
B. XML injection attack
C. Buffer overflow attack
D. SQL injection attack
CompTIA Security+ Question J-69
A security engineer is reviewing log data and sees the output below:
POST: /payload.php HTTP/1.1
HOST: localhost
Accept: */*
Referrer: http://localhost/
******* HTTP/1.1 403 Forbidden
Connection: close
Log: Access denied with 403. Pattern matches form bypass Which of the following technologies was MOST likely being used to generate this log?
A. Host-based Intrusion Detection System
B. Web application firewall
C. Network-based Intrusion Detection System
D. Stateful Inspection Firewall
E. URL Content Filter
CompTIA Security+ Question I-58
Without validating user input, an application becomes vulnerable to all of the following EXCEPT:
A. Buffer overflow.
B. Command injection.
C. Spear phishing.
D. SQL injection.
CompTIA Security+ Question I-54
The string:
‘ or 1=1–
Represents which of the following?
A. Bluejacking
B. Rogue access point
C. SQL Injection
D. Client-side attacks
CompTIA Security+ Question I-34
Highly sensitive data is stored in a database and is accessed by an application on a DMZ server. The disk drives on all servers are fully encrypted. Communication between the application server and end-users is also encrypted. Network ACLs prevent any connections to the database server except from the application server. Which of the following can still result in exposure of the sensitive data in the database server?
A. SQL Injection
B. Theft of the physical database server
C. Cookies
D. Cross-site scripting
CompTIA Security+ Question I-16
Which of the following is BEST at blocking attacks and providing security at layer 7 of the OSI model?
A. WAF
B. NIDS
C. Routers
D. Switches
CompTIA Security+ Question H-30
Which of the following BEST describes a protective countermeasure for SQL injection?
A. Eliminating cross-site scripting vulnerabilities
B. Installing an IDS to monitor network traffic
C. Validating user input in web applications
D. Placing a firewall between the Internet and database servers