A server (10.0.0.2) on the corporate network is experiencing a DoS from a number of marketing desktops that have been compromised and are connected to a separate network segment. The security engineer implements the following configuration on the management router:
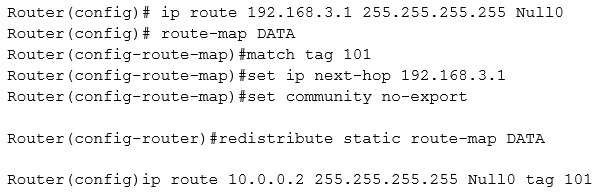
Which of the following is the engineer implementing?
A. Remotely triggered black hole
B. Route protection
C. Port security
D. Transport security
E. Address space layout randomization
CompTIA Advanced Security Practitioner (CASP) Question 50
After embracing a BYOD policy, a company is faced with new security challenges from unmanaged mobile devices and laptops. The company’s IT department has seen a large number of the following incidents:
– Duplicate IP addresses
– Rogue network devices
– Infected systems probing the company’s network
Which of the following should be implemented to remediate the above issues? (Choose two.)
A. Port security
B. Route protection
C. NAC
D. HIPS
E. NIDS
CompTIA Security+ Question H-98
A video surveillance audit recently uncovered that an employee plugged in a personal laptop and used the corporate network to browse inappropriate and potentially malicious websites after office hours. Which of the following could BEST prevent a situation like this form occurring again?
A. Intrusion detection
B. Content filtering
C. Port security
D. Vulnerability scanning
CompTIA Security+ Question G-83
Which of the following protocols provides transport security for virtual terminal emulation?
A. TLS
B. SSH
C. SCP
D. S/MIME
CompTIA Security+ Question G-68
An administrator needs to connect a router in one building to a router in another using Ethernet. Each router is connected to a managed switch and the switches are connected to each other via a fiber line. Which of the following should be configured to prevent unauthorized devices from connecting to the network?
A. Configure each port on the switches to use the same VLAN other than the default one
B. Enable VTP on both switches and set to the same domain
C. Configure only one of the routers to run DHCP services
D. Implement port security on the switches
CompTIA Security+ Question G-44
Which of the following can be used to maintain a higher level of security in a SAN by allowing isolation of mis-configurations or faults?
A. VLAN
B. Protocol security
C. Port security
D. VSAN
CompTIA Security+ Question F-39
The loss prevention department has purchased a new application that allows the employees to monitor the alarm systems at remote locations. However, the application fails to connect to the vendor’s server and the users are unable to log in. Which of the following are the MOST likely causes of this issue? (Select TWO).
A. URL filtering
B. Role-based access controls
C. MAC filtering
D. Port Security
E. Firewall rules
CompTIA Security+ Question E-63
A database administrator contacts a security administrator to request firewall changes for a connection to a new internal application. The security administrator notices that the new application uses a port typically monopolized by a virus. The security administrator denies the request and suggests a new port or service be used to complete the application’s task. Which of the following is the security administrator practicing in this example?
A. Explicit deny
B. Port security
C. Access control lists
D. Implicit deny
CompTIA Security+ Question D-64
A security administrator is tasked with ensuring that all devices have updated virus definition files before they are allowed to access network resources. Which of the following technologies would be used to accomplish this goal?
A. NIDS
B. NAC
C. DLP
D. DMZ
E. Port Security
CompTIA Security+ Question D-40
The Chief Information Security Officer (CISO) is concerned that users could bring their personal laptops to work and plug them directly into the network port under their desk. Which of the following should be configured on the network switch to prevent this from happening?
A. Access control lists
B. Loop protection
C. Firewall rule
D. Port security